There are a lot of tools for managing users in linux system. A lot of them. And judging by the number of Launchpad blueprints around the topic, there is also a lot of interest to improve Ubuntu’s user management infrastructure. Here at Opinsys we’ve been working with LDAP/kerberos for some years and although the situation has been getting better, there are still a lot of rough edges. It is possible to get complex desktop setups working nicely, but right now the invasion of web applications is reshaping the scene again.
I described some of the problems around the topic in my earlier blog postings:
What we currently need for ourselves is a dead simple user management tool that allows centralised management of the servers, but allows the administration access for the users to be split between schools. Usually there are a few people in every school who are responsible for managing the users for their own school. Often a single directory has user information for multiple schools and for various reasons it is not always desirable to show the user information for administrators in other schools. And of course everything on the web should integrate to it automatically. We are itching to do something about this.
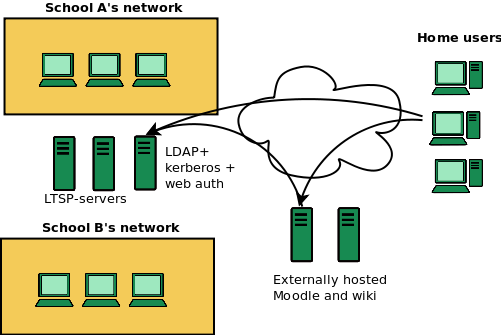
A common situation that we have right now in schools is something like this. Several schools share an ltsp cluster and an authentication server. Single server manages users for several schools and web applications hosted elsewhere authenticate against the district’s server.
I had a quick look at different blueprints around the topic in Launchpad and found the following. I’m sure there are many more around the topic, but these describe the problem area quite well. Unfortunately only a few features have been implemented.
| Blueprint | Issues discussed in the blueprint |
|---|---|
| Find tools to maintain large deployments | Puppet, LDAP user management, Ebox |
| Edubuntu Portal Server as a Corporate Identity and Single Sign On solution | LDAP user management, user portal, CAS authentication for external web applications |
| Default LDAP DIT for user and group managment | Default LDAP directory structure |
| Architecture of a directory infrastructure | Directory structure, kerberos/SSO, indentity management, authorization, access control, accounting, auditing |
| easy to install and use domain for linux | LDAP server setup and management for users, samba, nfs, mail, dhcp, dns, etc.. |
| Managing the directory | User management tools, FreeIPA |
| Configuration of services to integrate with a directory | Service configuration, kerberos principal creation for clients, dns settings, service locating |
| Identity management reference/test config | Reference identity management environment deployable with Puppet, using OpenLDAP/MIT Kerberos, openldap-dit |
Looking at the blueprints above it’s clear that Puppet is the tool of choice for configuration management. Based on my good experiences with Puppet I’m excited to see what comes out of it as more and more people start using it. For identity management there is no clear winner. There’s no common understanding about ”standard” LDAP directory structure either. We have looked at many tools, but either they don’t support kerberos or they are all too technical. The end-user should not have to even know that there is LDAP in the background. Simplicity rules.
We have years old tools to manage our setups, but our goal is to make everything better integrated with Ubuntu/Edubuntu. Many of the tools need rewriting and we are now in the process looking at what has changed since the original tools were written years ago and put all our knowledge into improving the situation. The earlier blog entries about OpenLDAP are part of the process.
Our plan regarding user management tools for our environments looks something like this:
- Get a working set of scripts to setup OpenLDAP and MIT kerberos for school usage (based on the earlier blog articles) – similar to what openldap-dit does
- Create a web based tool to manage LDAP/Kerberos users in easy fashion
- Solution for password synchronisation problem (userPassword in LDAP, samba password and kerberos password should all be updated at once)
- Make LTSP servers and laptops authenticate against OpenLDAP/Kerberos (pam-ldapd, nss-ldapd, sssd)
- Write LDAP/kerberos configuration instructions for Moodle/Mediawiki/Zimbra/other common web applications used in schools
- Create CAS/OpenID server with kerberos SSO support (Firefox can be used to pass the kerberos ticket to the web server that turns it to web login)
We’ve been working on steps 1-3 already and we should be able to release something working really soon now. It’s been a rough road at times, but we are getting there.
There are still open questions like choice between Heimdal and MIT kerberos server. E.g. OpenLDAP has smbk5pwd overlay for Heimdal, but we are looking if a similar solution for MIT kerberos would be possible.
Veli-Matti Lintu

Viimeisimmät kommentit